When you’re developing websites at work, while you can set up a self-signed certificate to test pages over SSL, it’s better to use a trusted certificate which you can do for free if your employer has set up a CA certificate which you can sign against. Also, since certificates are only valid for one level of a domain, e.g. abdullahyahya.com is different from foo.abdullahyahya.com which is different from foo.bar.abdullahyahya.com, you can add Subject Alternative names to your certificate and wildcards like *.abdullahyahya.com, *.foo.abdullahyahya.com and *.foo.bar.abdullahyahya.com to use the same certificate over many domains.
Following are steps to set up a certificate with SANs on a Mac with Apache.
1. Install OpenSSL
$ brew install openssl
2. Create a private host key
$ cd /private/etc/apache2 $ sudo mkdir ssl $ cd ssl $ sudo ssh-keygen -f local.example.com.key
You can choose anything for the passcode, or leave it blank.
3. Edit Open SSL Configuration File
Copy /etc/pki/tls/openssl.cnf and save it as local.example.com.openssl.cnf.
Edit the new file and find the [ req ] section, and add the following:
req_extensions = v3_req
Then, make the [ v3_req ] section look something like this
[ v3_req ] # Extensions to add to a certificate request basicConstraints = CA:FALSE keyUsage = nonRepudiation, digitalSignature, keyEncipherment subjectAltName = @alt_names
Make a new section called [ alt_names ] which looks something like this
[ alt_names ] DNS.1 = *.example.com DNS.2 =*.local.example.com IP.1 = 127.0.0.1
3. Create a Certificate Signing Request (CSR)
Run the command
openssl req -new -nodes -keyout local.example.com.key -out local.example.com.csr -config local.example.com.openssl.cnf
Following the prompts to specify your country, state, location, company, etc. Optionally, specify a passphrase, if you want. This will generate a local.example.com.csr file.
4. Have the CSR Signed by Your CA and Download it in Base-64 Format
This process will depend on your employer’s setup. You will end up with a .crt which you can rename to local.example.com.crt
5. Get a Copy of Your Employer’s CA (Certificate Authority) Certificate
Get the CA cert in base-64 format and save it. I’ll call it abc-company-ca-cert.crt
6. Append the CA Cert to cert.pem
Copy and paste the contents of abc-company-ca-cert.crt to the end of /usr/local/etc/openssl/cert.pem
7. Edit Apache config
In httpd.conf, make sure to uncomment the line
Include /private/etc/apache2/extra/httpd-ssl.conf
8. Edit Apache SSL config
In httpd-ssl.conf, make sure to uncomment the line
SSLEngine on
and add the following lines in the appropriate places
SSLCertificateFile "/etc/apache2/ssl/local.example.com.crt" SSLCertificateKeyFile "/etc/apache2/ssl/local.example.com.key"
9. Edit Apache Virtual Hosts
In httpd-vhosts.conf, add the following to your <VirtualHost *:443> containers
SSLEngine on SSLCertificateFile /private/etc/apache2/ssl/localhost.crt SSLCertificateKeyFile /private/etc/apache2/ssl/localhost.key
10. Test Apache Config
$ sudo apachectl configtest Password: Syntax OK
11. Restart Apache
$ sudo apachectl restart
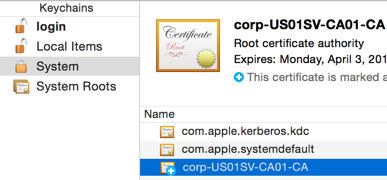
12. Add the CA Cert to Your KeyChain
Double-click abc-company-ca-cert.crt and add the CA cert to the “System” keychain
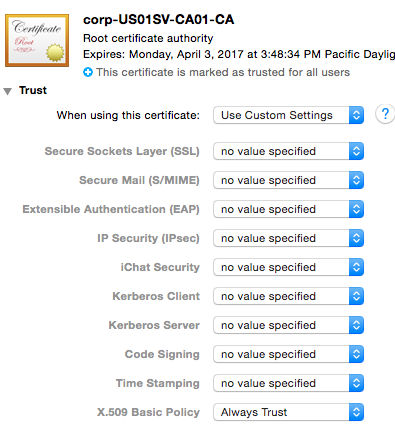
13. Specify the CA Cert’s Trust Settings
Edit the cert and set X.509 Basic Policy to “Always Trust”
14. Test in Chrome
In Chrome, go to a page like https://local.example.com/info.php. You should see a green https:// lock in the URL bar. If it’s not green, try clearing your Chrome browser history and cache, quitting Chrome and trying again.
15. Test in Safari
In Safari, go to a page like https://local.example.com/info.php. You should see a gray locked lock icon in the URL bar.
16. Test in Firefox
In Firefox, go to a page like https://local.example.com/info.php. You should see a gray locked lock icon in the URL bar. If you don’t see the correct lock, go to Firefox > Preferences > Advanced > View Certificates > Authorities > Import and import the abc-company-ca-cert.crt.